
Undergraduate and graduate students in Purdue University’s Polytechnic Institute presented posters summarizing their 2021-2022 research projects at Stewart Center in late April.
Students engaged in research affiliated with each of the Polytechnic’s strategic research impact areas (RIA), including Future Work and Learning, Holistic Safety and Security, and Realizing the Digital Enterprise. Titles and research abstracts for Holistic Safety and Security (HSS)-affiliated projects are listed here.
“The breath and diversity of topics covered in these posters made quite an impression,” said Yingjie “Victor” Chen, associate professor of computer graphics technology and co-leader of the HSS research impact area. “Safety and security involve in research in almost all of the departments in our college. There are so many collaboration opportunities within our college, across the Purdue campus, and extending to the broad community.”
Holistic Safety and Security
Geetanjali Bihani, “Permutation-based Privacy in Text Vectors”
Abstract: With data privacy becoming more of a necessity than a luxury in today's digital world, research on more robust models of privacy preservation and information security is on the rise. In this work, we propose a Vector Space Steganography (VSS) method, which obfuscates private information encoded within word vectors. This method aims to minimize membership inference and training data extraction attacks, to prevent an eavesdropping adversary from learning about the sensitive features in the text, through the word vectors. We believe that this work will act as an appropriate framework to build more resilient models of privacy for language representations, working towards instilling security within natural language-based neural models.
Zhiwen Cao, “Vector-based Representation to Enhance Head Pose Estimation”
Abstract: Head pose estimation (HPE) refers to the task of estimating of human head orientation from a single image. It has important applications in fields such as driver attention warning (DAW) system, surveillance system, etc. Currently researchers use Euler angles to describe the human head orientation. More specifically, they decompose the rotation into three orthogonal parts: pitch, yaw and roll.
Jiahui Dong, “CryoVR - Virtual Reality Augmented CryoEM Training”
Abstract: Cryogenic electron microscopy (CryoEM) has emerged as a revolutionary method for solving high-resolution structures and studying the dynamics of macromolecular complexes and viruses in near-native states. However, the availability of the equipment and the time and cost needed for training severely limit the opportunity of training. To solve these problems, we developed a virtual reality-based training system, CryoVR, to prepare trainees before operating real world CryoEM equipment.
This paper describes the design and assessment of CryoVR, which helps users learn CryoEM experimental procedures in a virtual environment, allowing immersive training with step-by-step tutorials with vivid visual, audio, and text guidance. Implemented as a training step before a novice user interacts with expensive real-world CryoEM equipment, CryoVR can help users become familiar with hands-on operational procedures through multiple training modules and earning certificates after passing the built-in exam mode. Qualitative evaluation and feedback of CryoVR from users with various levels of CryoEM experience indicate the substantial value of CryoVR as a tool for a comprehensive CryoEM procedural training.

Rey Gonzalez, “Employing Humor to Enhance Cyber Security Education”
Abstract: In this study, authors explore phishing and smishing feature exploitation by asking one (or two) important question(s): How can we improve cyber security education? Specifically, can humor help better communicate and encourage a perspective of defensive cyber hygiene and social engineering awareness? By comparing information retention among students after being trained on common phishing and smishing features, cybersecurity education experts will be better prepared in how these features are communicated.
Xiaolei Guo, “Heuristic Evaluation Methods for VR Training Systems”
Abstract: With the continuing expansion of the use of VR technology for serious purposes, creators inevitably raise concerns about the usability aspects of the systems, resulting in an increased need for more efficient usability evaluation. Heuristic evaluation (HE) methods are among the most widely used usability inspection methods in the human-computer interaction (HCI) domain. Although research and practice adopting the HE methods are growing within the VR community, we lack insights into how practitioners perform the technique and its applicability for VR studies.
Prior studies adopting HE methods in VR studies mainly shed light on modifying heuristics/principles, but they leave problems with the HE methods conducted process. Therefore, it is crucial to understand how evaluators apply HE methods to VR systems and what challenges they are encountered. Such an understanding would inform the design of HE methods and tools that could potentially help practitioners better analyze VR systems.
Shinelle Hutchinson, “Investigating the Health of Wearables,”
Abstract: Wearable devices are becoming more and more prevalent in our daily lives as people become more curious about how well they are doing in monitoring, improving, or maintaining their health and fitness. Fitness trackers and smartwatches have become almost ubiquitous, so these devices have begun to play critical roles in forensic investigations.
In this paper, we conducted a forensic analysis of the controlling applications for two popular fitness bands (i.e., Amazon Halo and Garmin Connect) on an Android smartphone device to (1) provide forensic investigators with a roadmap of forensically relevant data that are stored within these applications and (2) highlight any privacy concerns that the stored data within these applications may present to the applications’ users.
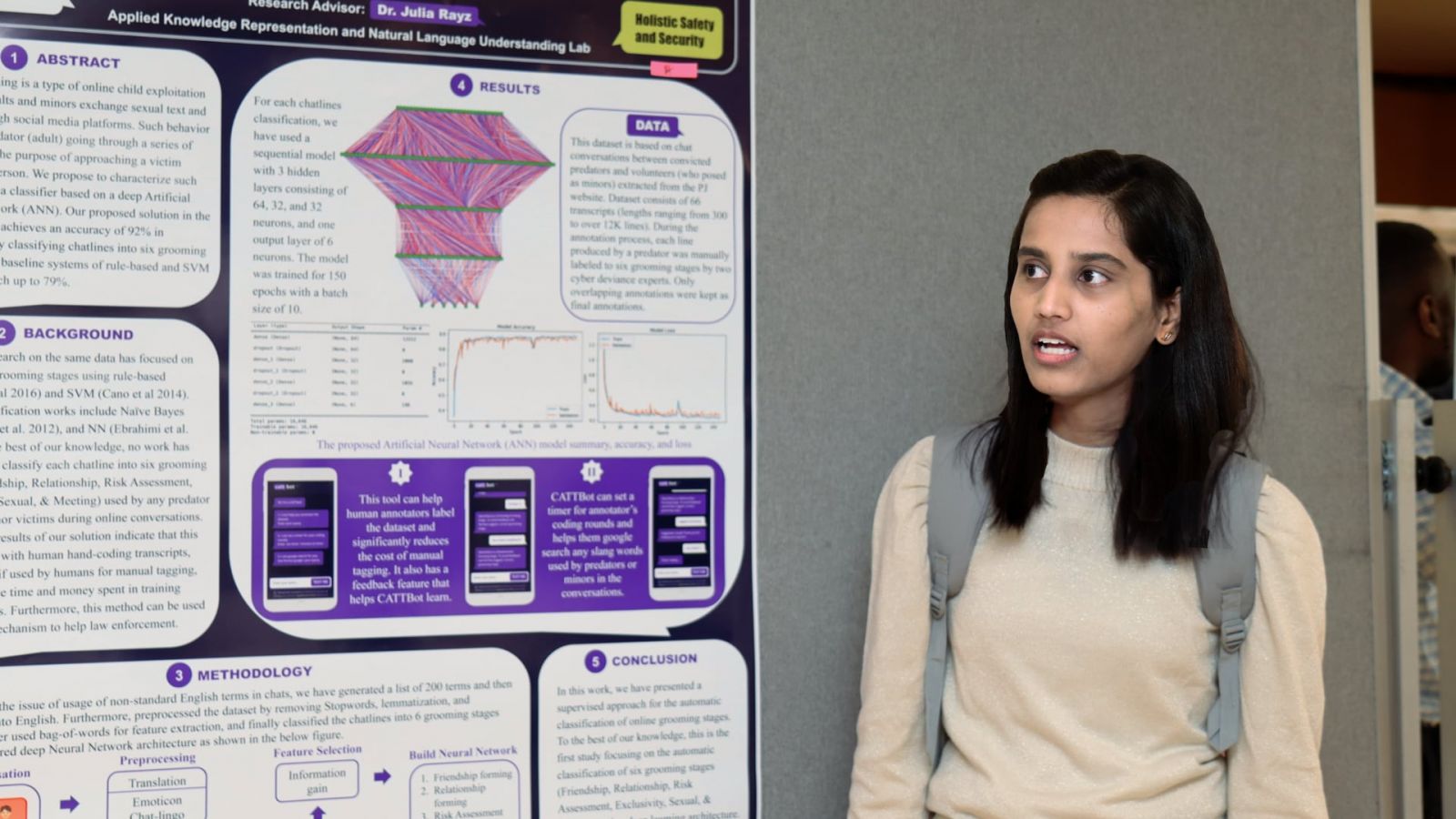
Sweta Kesur, “Deep Learning AI chatbot to classify grooming stages”
Abstract: Child grooming is a type of online child exploitation in which adults and minors exchange sexual text and media through social media platforms. Such behavior entails a predator (adult) going through a series of stages with the purpose of approaching a victim (minor) in person. We propose to characterize such stages using a classifier based on a deep Artificial Neural Network (ANN). Our proposed solution in the experiments achieves an accuracy of 92% in automatically classifying chatlines into six grooming stages while baseline systems of rule-based and SVM can only reach up to 79%.
Zuotian Li, “Visual Analytics system for Explainable Medical Patient Trajectory From Graph Neural Network (GNN)”
Abstract: The overall prevalence of chronic kidney disease (CKD) in the general population of the United States is approximately 14% in 2021. When people get CKD, their kidneys become damaged and over time may not clean the blood as well as healthy kidneys. Besides the development of medical diagnosis in the medical area, machine learning (ML) has shown great promise for medical assessments thanks to the rapid rise of electronic health records (EHRs). Data-driven studies, such as prescription recommendations and medical events can be predicted by the machine model built on the EHRs data.
Researchers have proposed to use Graphic Neural networks (GNNs) to help clinicians to make decisions by predicting the patient disease risk, prescriptions and physical index. However, without the explanations for machine decisions and predictions, the clinicians would not understand and justify the reliability of the results due to the Blackbox nature of the AI or GNNs. This research aims to enable medical researchers or clinicians to understand, appropriately trust and effectively manage the GNNs using visualization.
Gianna Lint, “Applying Risk Assessment Principles to the Sex Trafficking Process”
Abstract: Sex trafficking is the fastest growing organized criminal activity. Trafficking organizations operate as a business, driven by profit and providing a service due to existing demand. This study examined the feasibility of applying Six Sigma principles to sex trafficking from a business operations perspective.
A business process map was developed that prioritized activities to identify process steps with the potential for disruption. The most common failure modes identified were the trafficker or customer being caught, followed by the victim being rescued. A Six Sigma approach appears to be a viable framework in understanding sex trafficking as a business.
Tanmay Surve, “A Crowd Sensing Approach to Detect Road Anomalies”
Abstract: Various types of damage may occur on road surfaces owning to external factors, such as weather, overloaded vehicles, and traffic volume, as well as internal factors, such as defects in materials and cross-sections. This long-term deterioration affects not only the safety and satisfaction of road users but also the economic efficiency. Our research aims at utilizing smartphones, machine learning and crowdsourcing for the collection and analysis of a great amount of field data from numerous users (e.g., drivers) whilst driving on roads. The frequent reporting on a daily/hourly basis can be used to inform the relevant stakeholders for timely road maintenance, aiming to ensure the road’s serviceability at a lower inspection and maintenance cost.
Ziyang Tang, “FileTSAR+: An Elastic Network Forensic Toolkit for Law Enforcement”
Abstract: The Toolkit for Selective Analysis & Reconstruction of Files (FileTSAR) was created in 2018 as a forensically sound investigative tool that processes large-scale computer networks for digital evidence by selectively capturing data flows, analyzing the contents of those flows and reconstructing multiple types of data.
Chi Tian, “A Case Study of Drivers’ Visual Attention and Behavioral Responses to Traffic Signs or Other Delineation Devices on A Curved Section”
Abstract: In 2017, there were 911 traffic fatalities in Indiana, an historic high in the last ten years (IIPPI, 2017). Driver-related factors accounted for 87% of collisions in 2016 and 2017 as well as 95% of fatal collisions in 2016 and 96% of fatal collisions in 2017 (IIPPI, 2016, 2017). Three attention-related issues result in “looked but failed to see” driver errors (Knowles & Tay, 2002). This study aims to compare countermeasures in high-risk areas in Indiana; practical solutions will be provided to LTAP at the end of study. With the implementation of this study, more objective evidence will be provided to support countermeasures that could reduce traffic accidents effectively in Indiana. Moreover, the project can provide a thorough understanding of how different countermeasures affect drivers’ eye movements and driving performance.
Damin Zhang, “Examining Stereotypes in News Articles”
Abstract: Gender biases or stereotypes have been studied in short text and manually labeled corpora, but little work has been done in real-world unlabeled text corpora like news articles. This work investigated news articles from mainstream U.S. media outlets ranging from 2013 to early 2020. We used structural topic modeling to estimate gender prevalent topics, compared the results with topic modeling embedding, and incorporated qualitative and quantitative analyses to understand the appearance of gender stereotypes in news articles from each gender group.
The structural topic modeling results showed that gender prevalent topics align with stereotypical representations of either gender group, and media outlets with imbalanced gender distribution are more influential on stereotypical representations. The topic modeling embedding results support prior results and provide additional information supporting the conclusion.
Yi Zhang, “Can Visual Linguistic Models become a Knowledge Base: A Preliminary Study on Size Prediction”
Abstract: Empowering machines to understand our physical world should go beyond models with only natural language and models with only vision. Vision and language comprise a growing field of study that attempts to bridge the gap between natural language processing and computer vision communities by enabling models to learn visually grounded language. However, as an increasing number of pre-trained visual linguistic models focus on the alignment between visual regions and natural language, it is difficult to claim that these models capture certain properties of objects in their latent space, such as size.
Inspired by recent trends in prompt learning, this study will design a prompt learning framework for two visual linguistic models, ViLBERT and ViLT, and use different manually crafted prompt templates to evaluate the consistency of performance of these models in comparing the size of objects.
Additional information
- Student researchers present Future Work and Learning projects at spring poster session
- Student researchers present Realizing the Digital Enterprise projects at spring poster session (1 of 2)
- Student researchers present Realizing the Digital Enterprise projects at spring poster session (2 of 2)
- Purdue Polytechnic’s Strategic Research Impact Areas
- Purdue Polytechnic Office of Research
- Purdue Polytechnic’s Holistic Safety and Security research projects receive national attention, funding
- Future Work and Learning research projects focus on all human-technology interactions
- Realizing the Digital Enterprise researchers pair technology, social responsibility
- Undergraduate researchers present projects at fall expo
